It’s totally possible to use OAuth2 with AD FS to authenticate open-source Grafana logins. I’m sharing some mildly redacted config from my on-prem setup in hope of helping someone else.
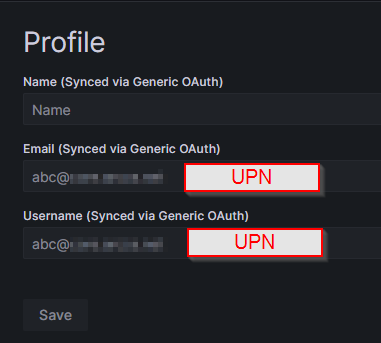
This guide will get you 95% done and able to sign in, but you won’t have Display Name and email loaded. Please contact me if you find a solution.
AD FS Config
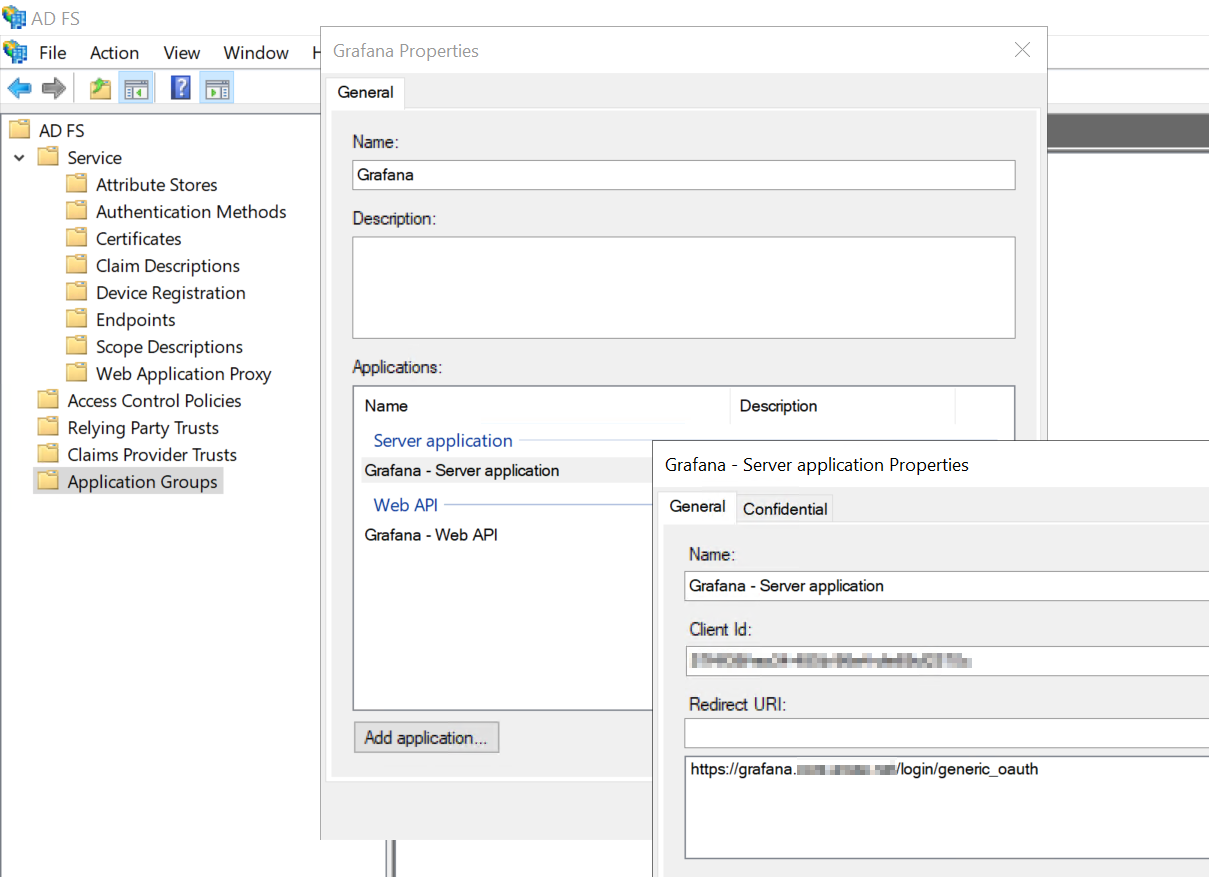
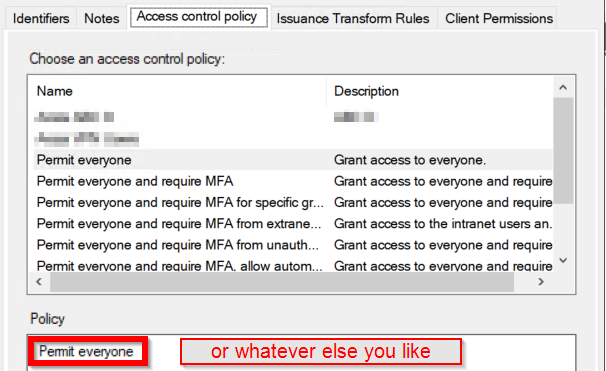
Add an application in Application Groups. You’ll need to make a Server application and a Web API.

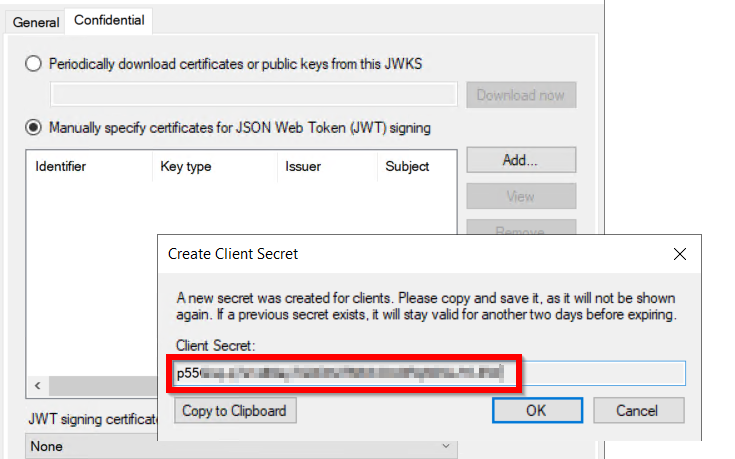
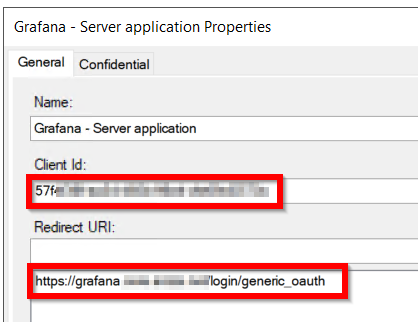
The server application should contain the below. Note the Client Secret for later to add in grafana.ini.
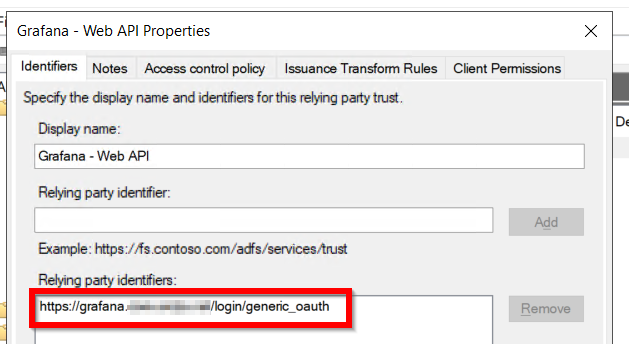
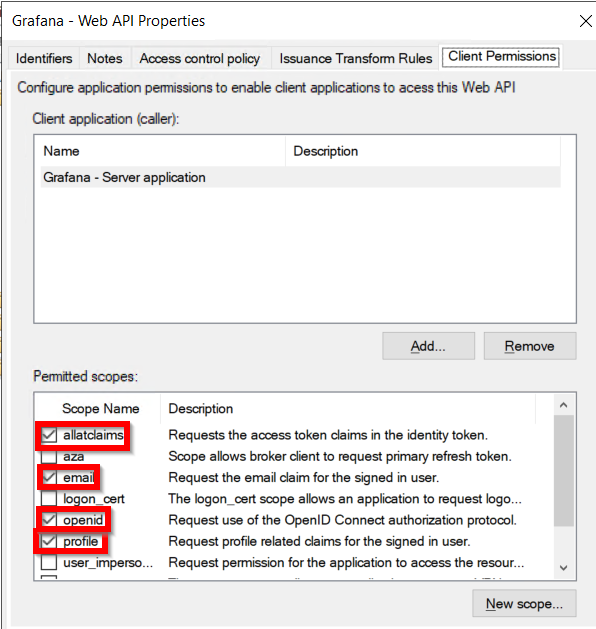
The Web API should look like this:
grafana.ini config
[auth.generic_oauth]
api_url = https://<adfs.domain.com>/adfs/userinfo
auth_url = https://<adfs.domain.com>/adfs/oauth2/authorize
client_id = 57fXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
client_secret = p55XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
enabled = true
name = Identity Services
scopes = openid
token_url = https://<adfs.domain.com>/adfs/oauth2/tokenRestart Grafana after editing grafana.ini.
Testing
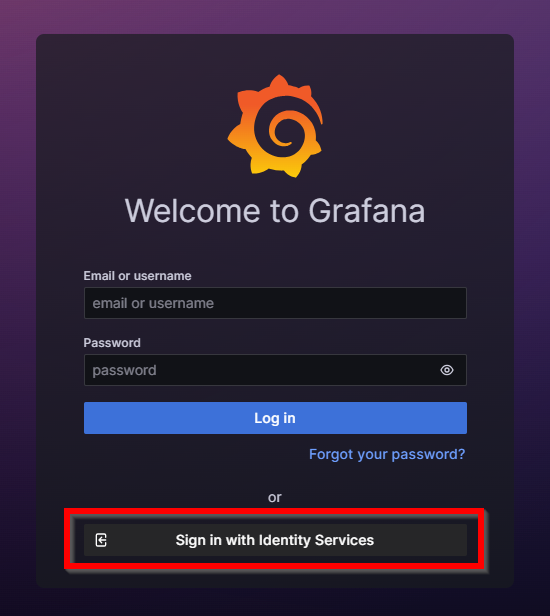
I click my button Identity Services and I’m logged in immediately.
Not perfect however – email and display name aren’t there, but it’s better than LDAP!
A note to Grafana
Yeah, it would have been nice to just use SAML, but for on-prem folks who don’t want to use the cloud, you appear to provide it exclusively for Enterprise customers only, which is priced horribly for small deployments. If you’re serious about security, unbundle SSO completely from product “nice-to-haves” and provide basic security for everyone as standard.